On This Day in Tech History
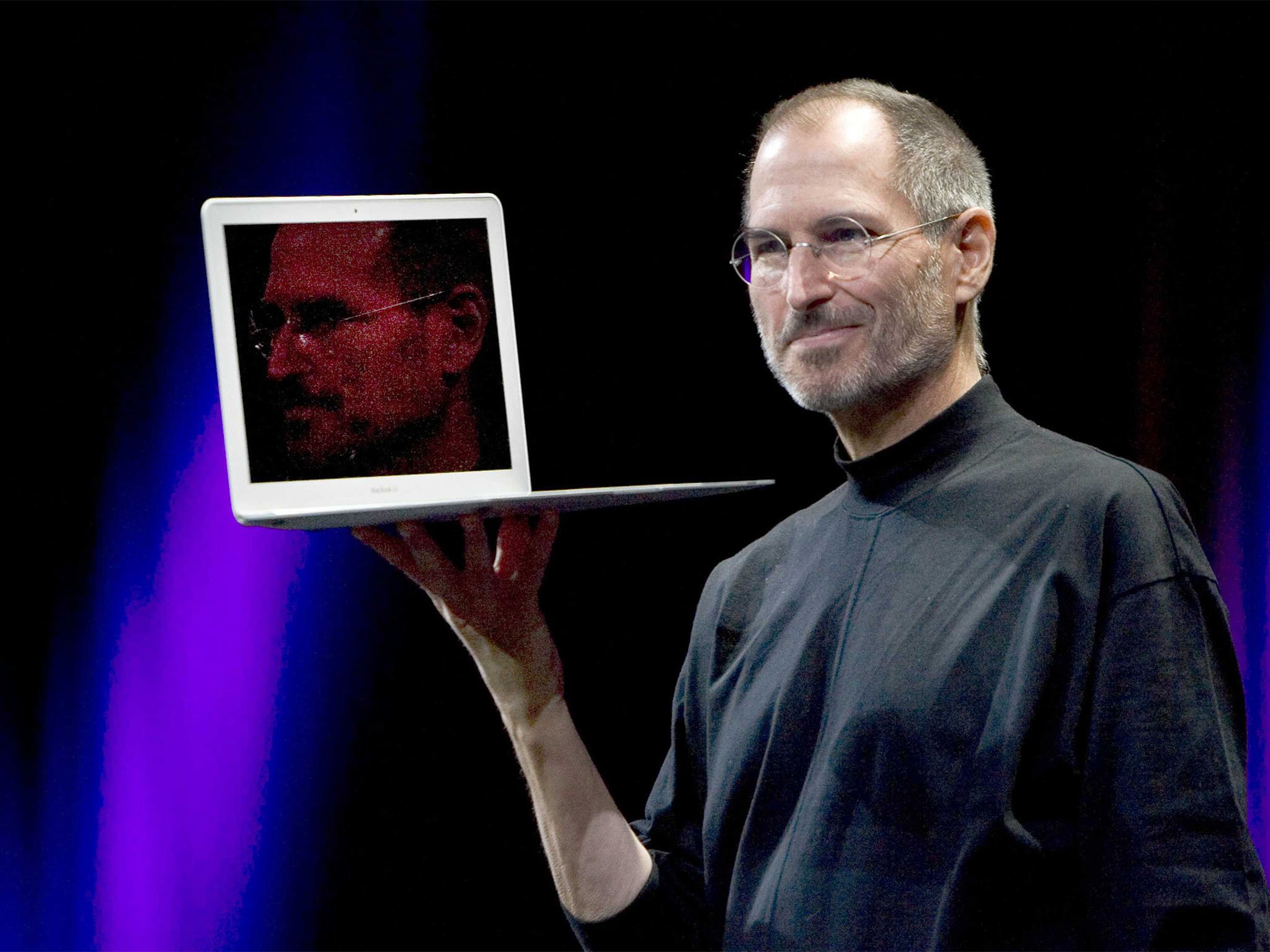
Steve Jobs unveiled the MacBook Air
2008Steve Jobs unveiled the MacBook Air, a super-thin and lightweight laptop computer that was marketed as the "world's thinnest notebook." The MacBook Air was praised for its sleek design and portability, and it helped to establish Apple's reputation as a leader in the tech industry

King Louis XVI of France was executed
1793King Louis XVI of France was executed by guillotine during the French Revolution. He had been tried and convicted of high treason by the National Convention, which had abolished the monarchy and established a republic in France. Louis' execution marked the end of an era and solidified the power of the revolutionary forces.

The first nuclear-powered submarine was launched
1954The first nuclear-powered submarine, the USS Nautilus, was launched in Groton, Connecticut. The Nautilus revolutionized undersea warfare and exploration, setting numerous records for speed and distance traveled. Its success paved the way for the development of other nuclear-powered submarines and ships.
3 Major Python Problems and How to Solve Them
January 21, 2023
All DC Movies Coming Out in 2023
January 21, 2023
MEANS OF FERTILISATION
January 21, 2023
The Rising Importance of First-Party Oracles
January 21, 2022
Who Really Owns Web3
January 21, 2022
Is Satoshi Nakamoto Back?
January 21, 2022
Npm globals as local dependencies
January 21, 2018
Measurement Malpractice
January 21, 2018
Docker Saves My Life
January 21, 2018
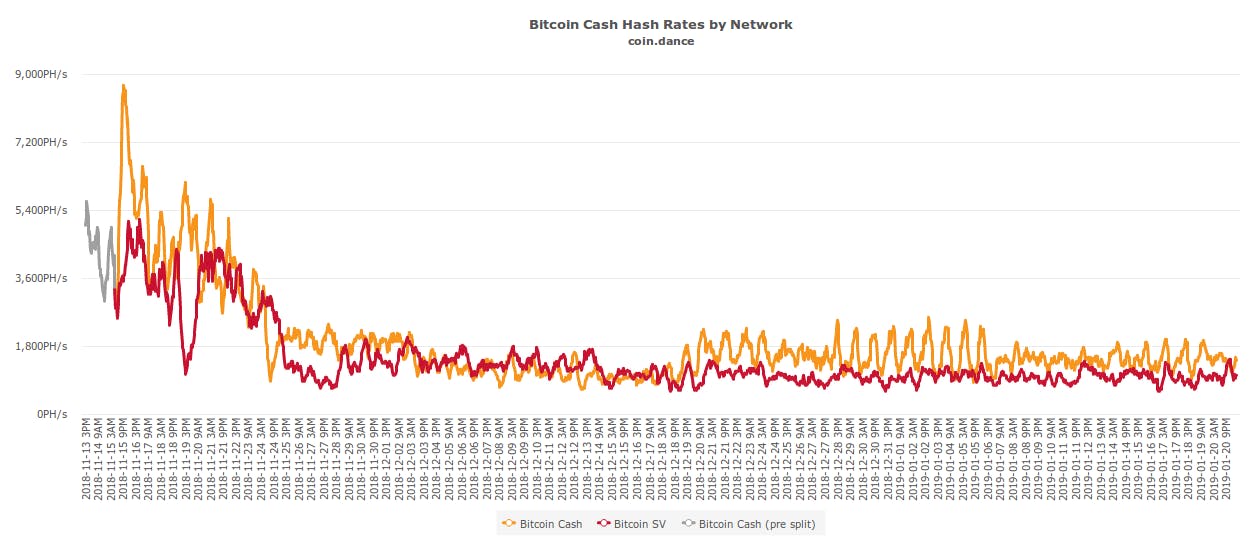
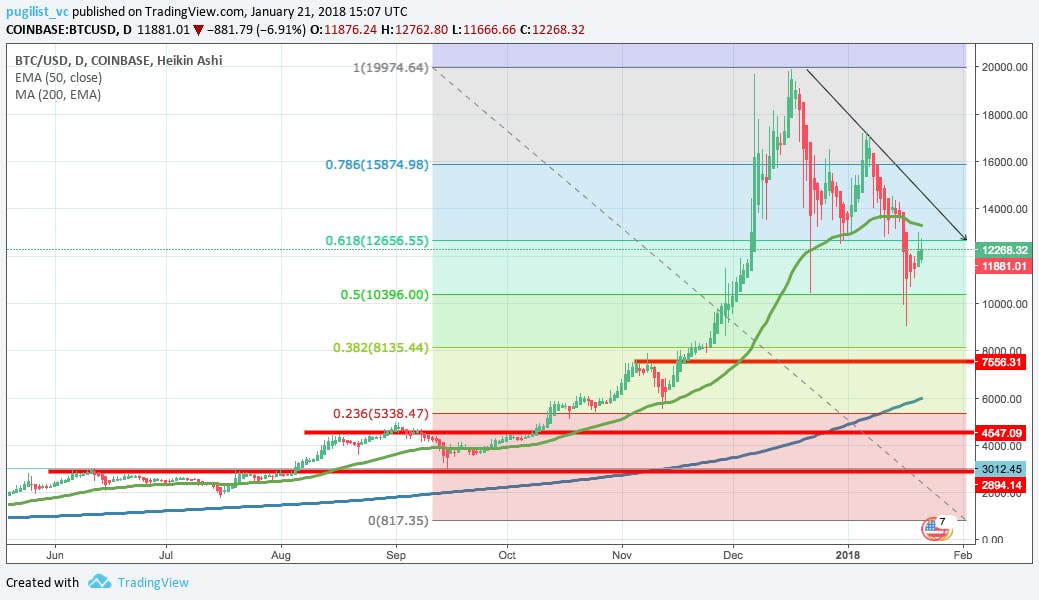
Chaos vs. Order — The Cryptocurrency Dilemma
January 21, 2018
Shit Programmers Say, Translated
January 21, 2018
Breathing Life into Bizly
January 21, 2016
Startup Eras
January 21, 2016
How UX is The Right Way to increase sales
January 21, 2016
Pair Programming: A (Semi-) Definitive Guide
January 21, 2016