388 reads
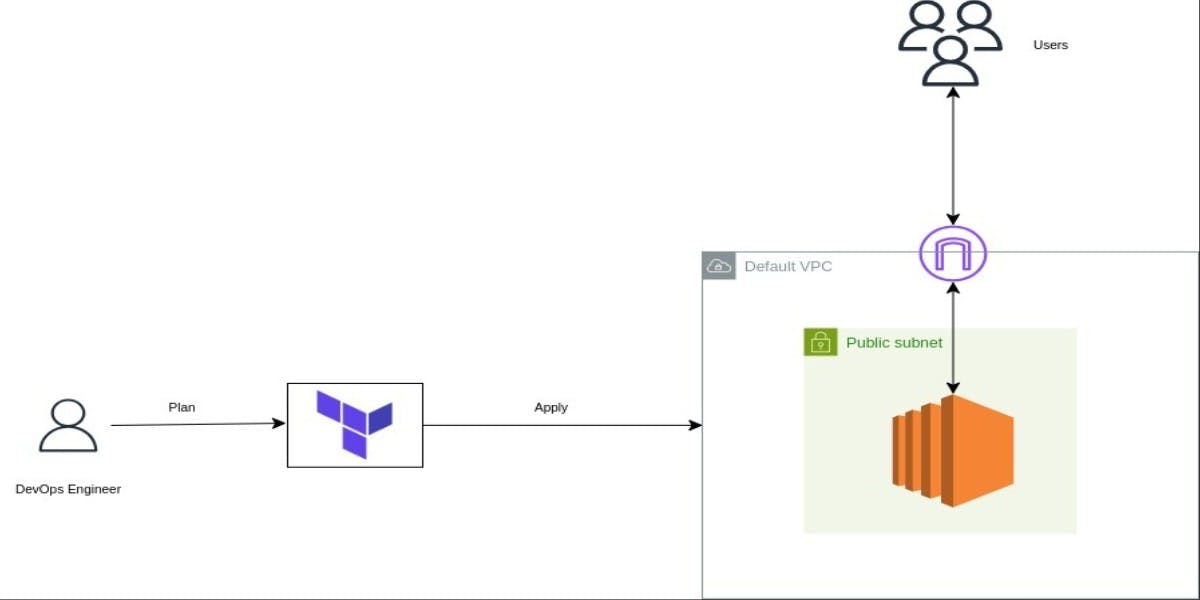
Automate EC2 Deployments on AWS with Terraform Modules
by
December 23rd, 2024
Audio Presented by

Software engineer passionate about sharing knowledge through writing and open-source contributions.
Story's Credibility

About Author
Software engineer passionate about sharing knowledge through writing and open-source contributions.