272 reads
Tips to Ensure the Prevention of Spoofing, Phishing, and Spam in Google Workspace
by
September 7th, 2021
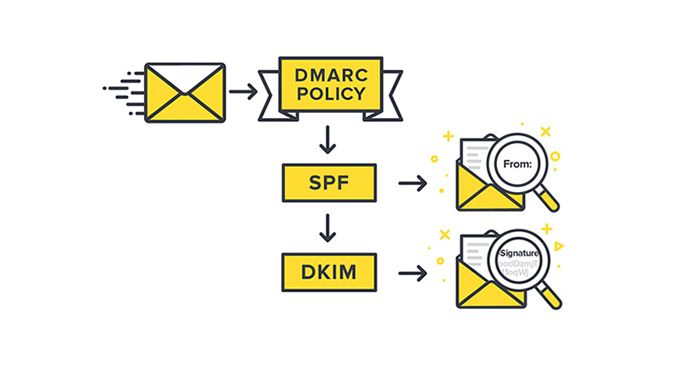
This company is providing you Securing your email & domain with SPF, DKIM and DMARC related Blog ·
About Author
This company is providing you Securing your email & domain with SPF, DKIM and DMARC related Blog ·
