296 reads
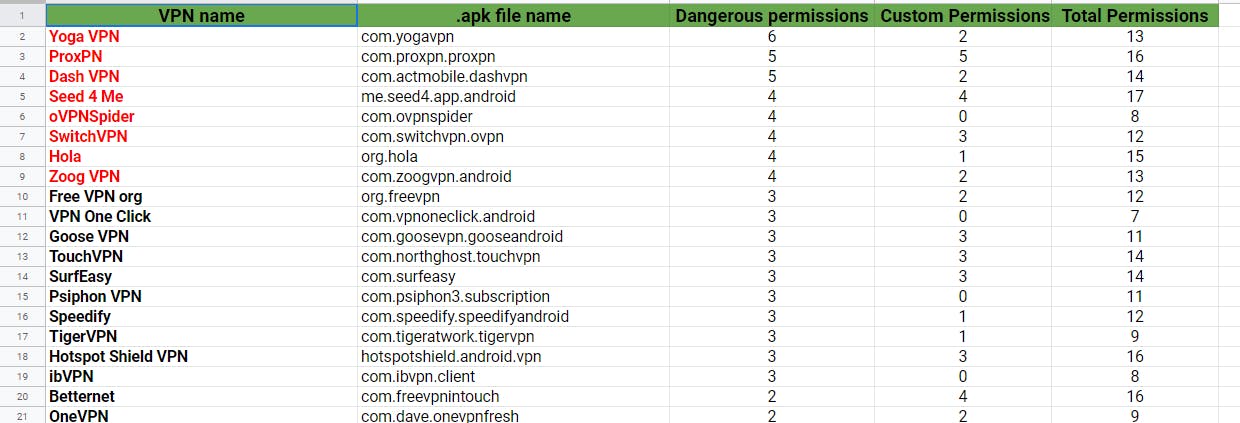
Recent Study Reviews The Different Permissions Requested by Android VPN Apps: The Result Was…
by
March 27th, 2019

Entrepreneur, Content Marketing Consultant. Founder and CEO of Digitage.net
About Author
Entrepreneur, Content Marketing Consultant. Founder and CEO of Digitage.net