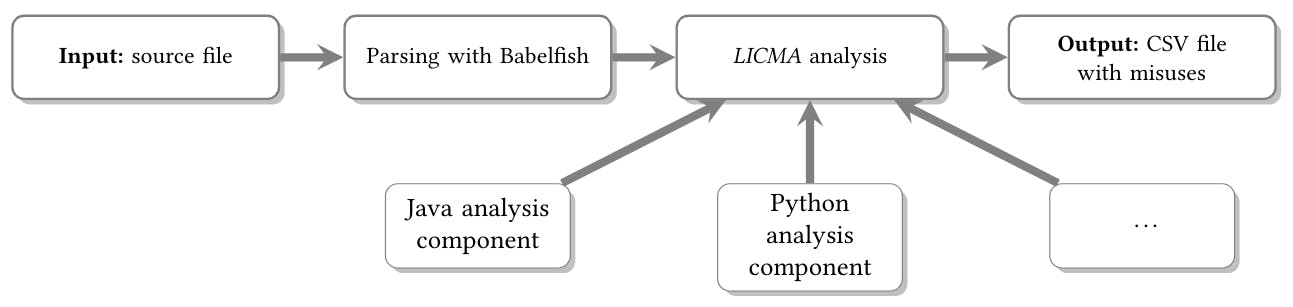
122 reads
Python Crypto API Misuses in the Wild: Design and Implementation of LICMA
by
May 6th, 2024
Audio Presented by

We believe everyone should have ultimate control and ownership over their cryptographic assets and digital transactions.
Story's Credibility

About Author
We believe everyone should have ultimate control and ownership over their cryptographic assets and digital transactions.
Comments
TOPICS
Related Stories
API Choice Overload
May 05, 2021
API Choice Overload
May 05, 2021