375 reads
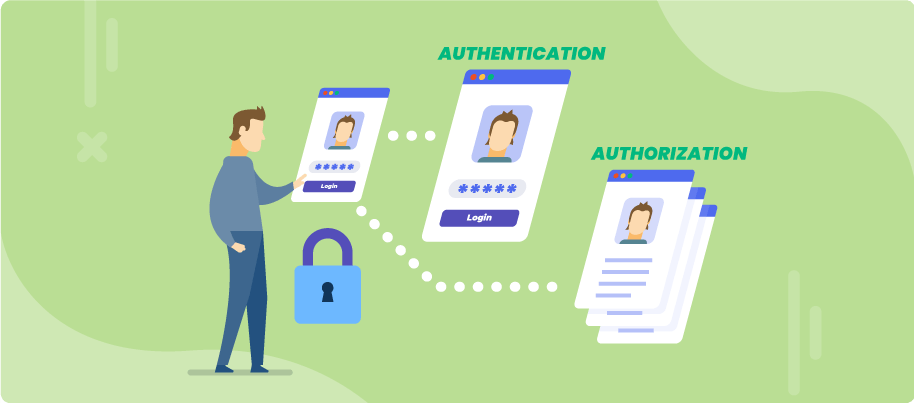
OAuth Vulnerabilities: How To Implement Secure Authorization in Your Web Application
by
February 28th, 2021

Software Engineer, Entrepreneur and Writer. Passionate about web development, security, and robust engineering.
About Author
Software Engineer, Entrepreneur and Writer. Passionate about web development, security, and robust engineering.