183 reads
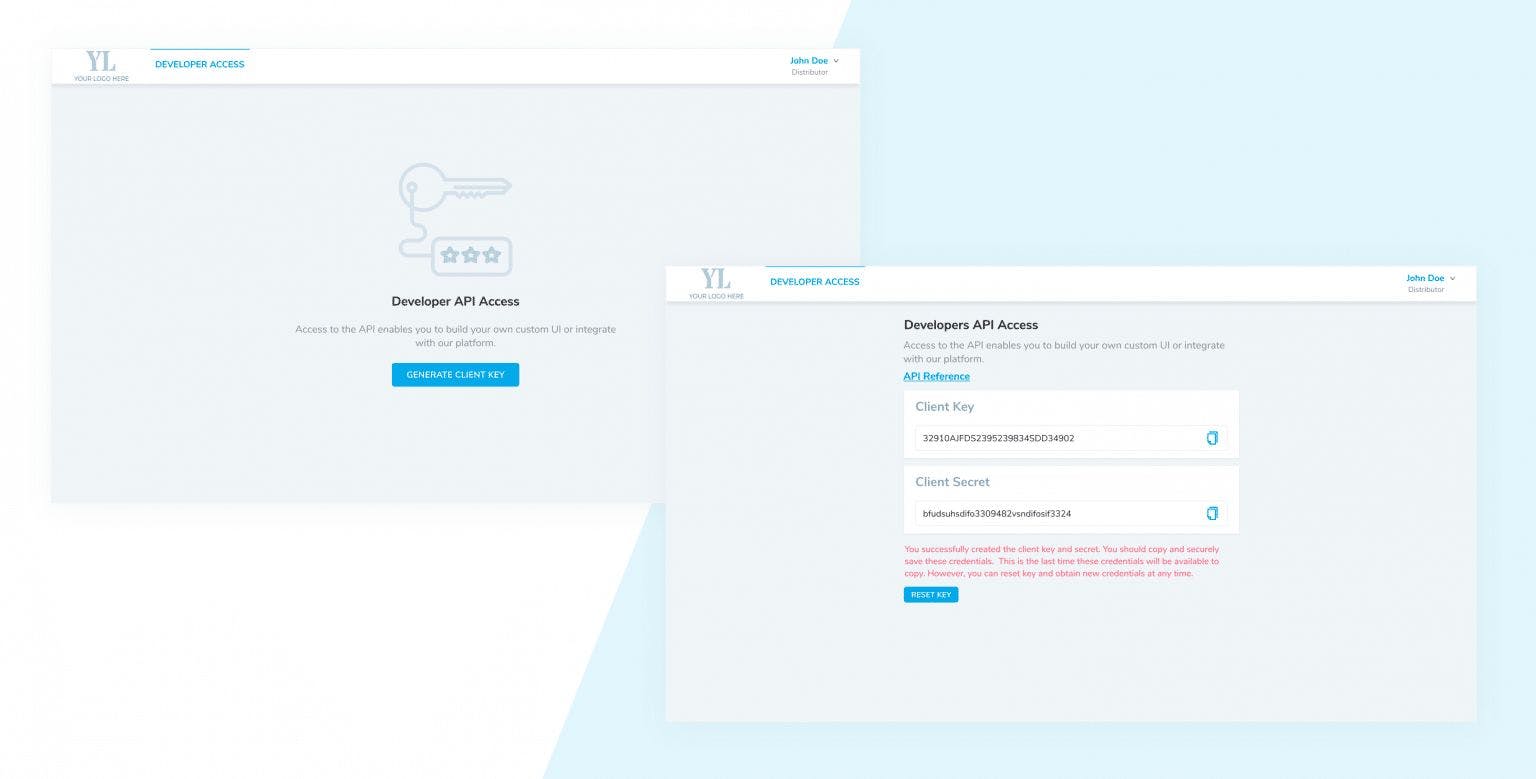
How to Provide Developer API Access for your SaaS Product Users
by
April 26th, 2021

We’re design-thinking product development experts, enabling entrepreneurs to convert ideas into launchable products
About Author
We’re design-thinking product development experts, enabling entrepreneurs to convert ideas into launchable products