28,979 reads
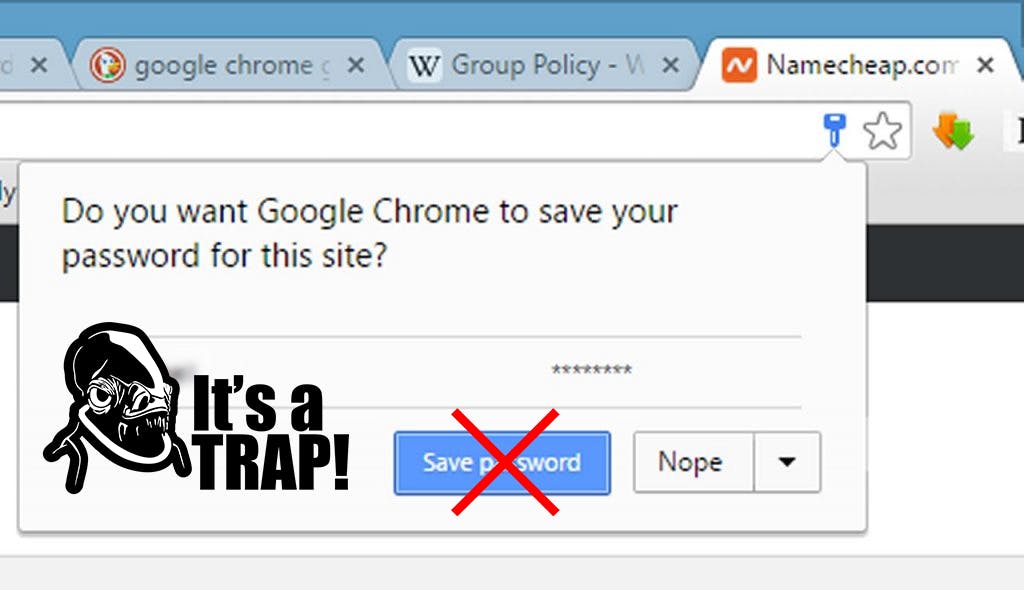
Why You Should Never Save Passwords on Chrome or Firefox
by
March 29th, 2019
Audio Presented by

Former CEO, Web3 Evangelist, & 2019 Noonie Winner. After years of hiatus, it's good to be back just DAOin' it.
About Author
Former CEO, Web3 Evangelist, & 2019 Noonie Winner. After years of hiatus, it's good to be back just DAOin' it.