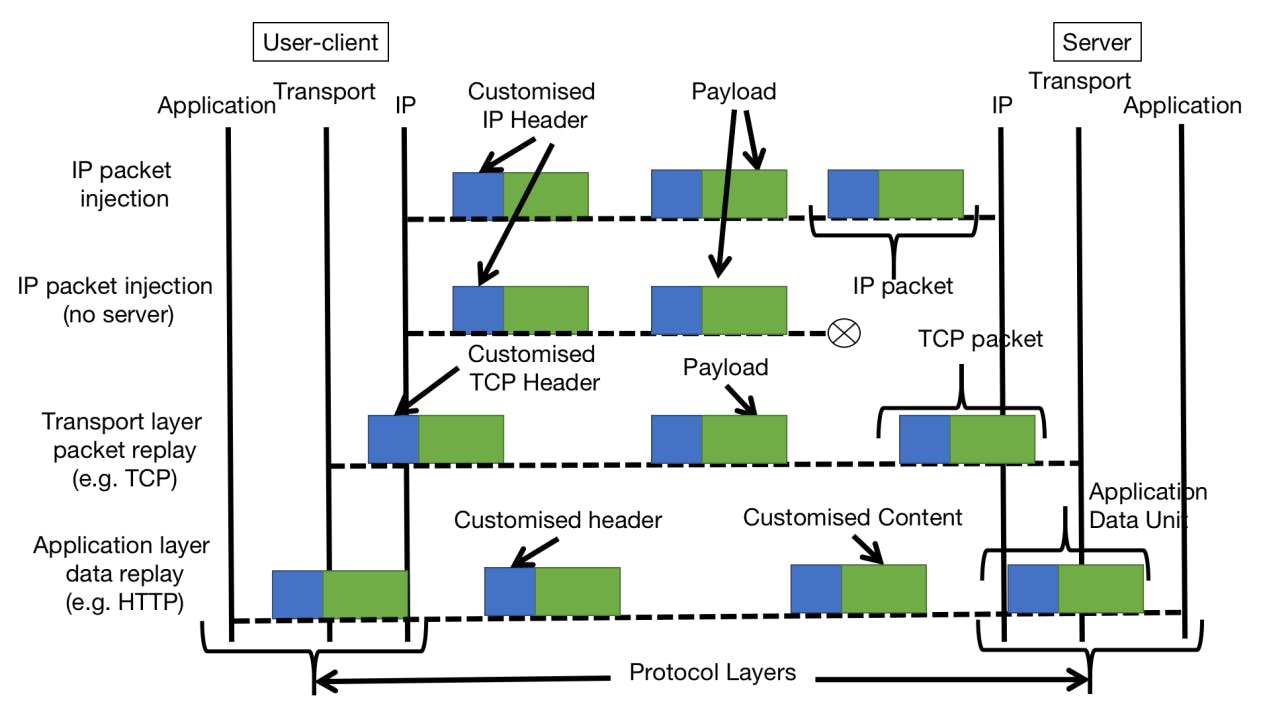
133 reads
Techniques for Detecting Discrimination in Streaming Services
by
April 11th, 2024
Audio Presented by

At NetNeutrality.Tech we treat all data on the Internet the same way and all users have equal access to online content.
Story's Credibility

About Author
At NetNeutrality.Tech we treat all data on the Internet the same way and all users have equal access to online content.