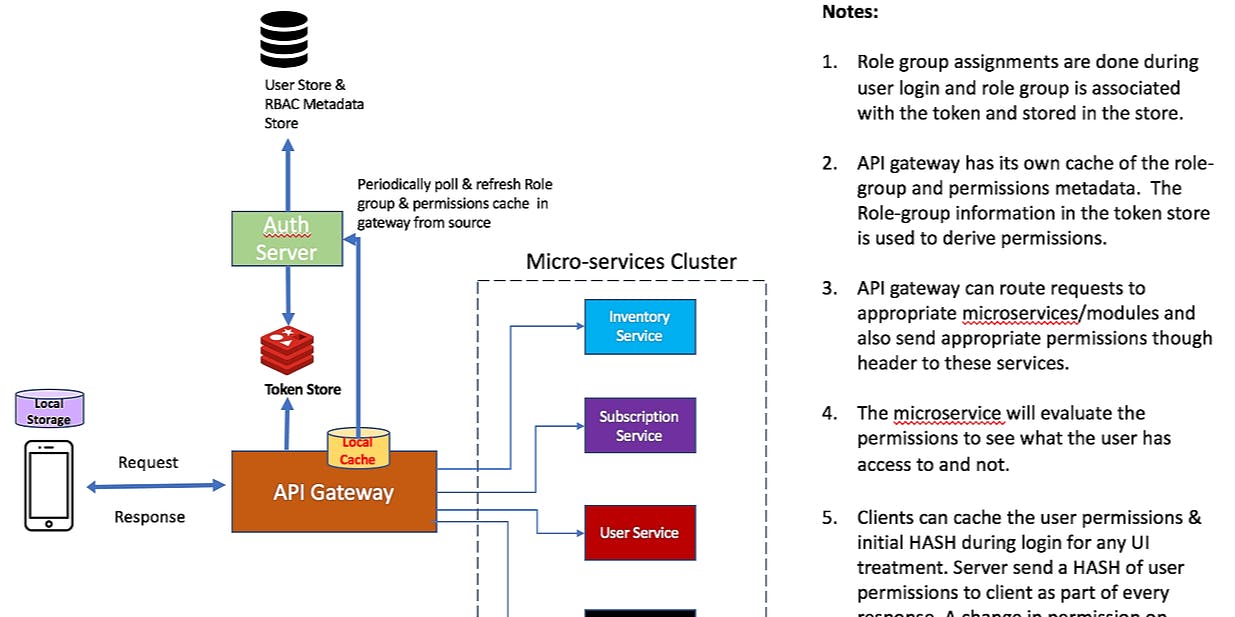
1,087 reads
ROLE BASED ACCESS CONTROL (RBAC) DESIGN FOR MICROSERVICES
by
September 20th, 2019
About Author
Large Scale Distributed Computing Architect
Comments
TOPICS
Related Stories
5 Reasons Traditional Security Tools Fall Short in Protecting APIs
@rossmoore
Jul 07, 2023