823 reads
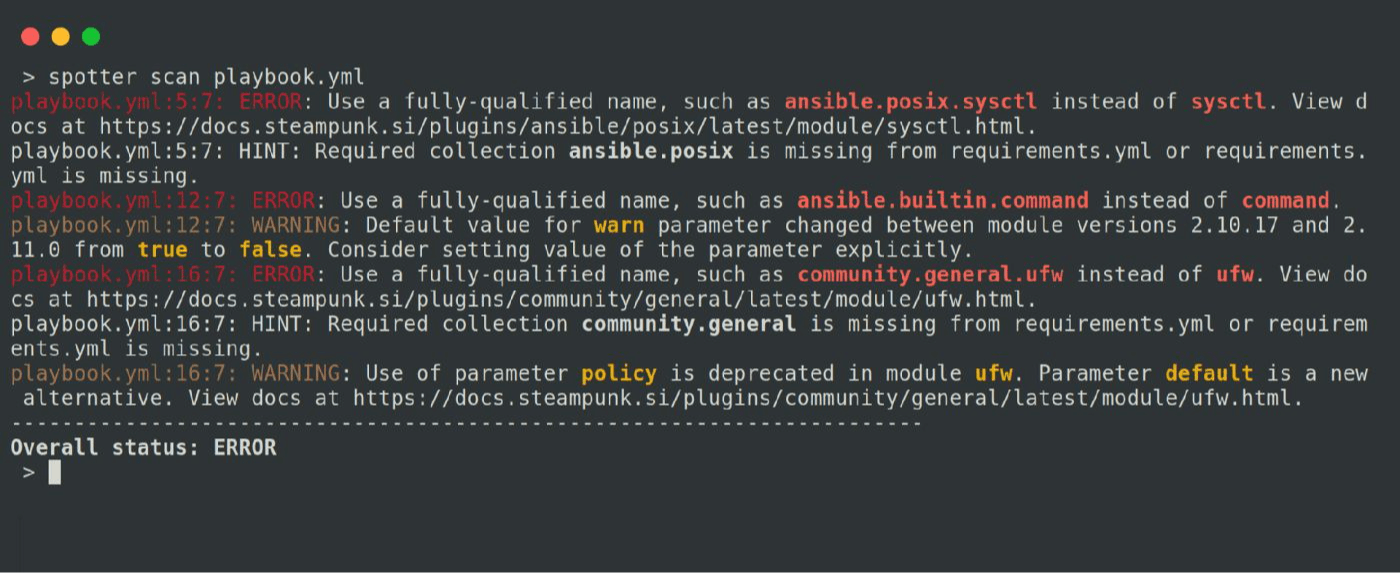
How to Make Ansible Playbooks Reliable and Secure
by
June 7th, 2023
Audio Presented by

Part of Steampunk Spotter team. Helping you put your playbooks under the Spotlight.
Story's Credibility

About Author
Part of Steampunk Spotter team. Helping you put your playbooks under the Spotlight.