ADVERSA
Adversa's stories on HackerNoon
Technology evolves every day, impacting our lives more and more. Don’t miss out on the tech of tomorrow via these remarkable technology stories.
Beyond Adversarial Training: A Robust Counterpart Approach to HSVM
Sun Jan 18 2026 By Hyperbole

BreachLock Expands Adversarial Exposure Validation (AEV) To Web Applications
Thu Jan 15 2026 By CyberNewswire

Adversarial Attacks on Large Language Models and Defense Mechanisms
Mon Dec 01 2025 By Prakash Velusamy

Methodology for Adversarial Attack Generation: Using Directives to Mislead Vision-LLMs
Tue Sep 30 2025 By Text Generation

Typographic Attacks on Vision-LLMs: Evaluating Adversarial Threats in Autonomous Driving Systems
Sat Sep 27 2025 By Text Generation

Shadow Injection and Adversarial Testing in Tool-Augmented Agents
Wed Aug 13 2025 By Sal Kimmich

A Model for Blockchain Mining Under Adversarial Conditions
Tue Jul 01 2025 By EScholar: Electronic Academic Papers for Scholars

Unified Speech and Language Models Can Be Vulnerable to Adversarial Attacks
Thu Feb 06 2025 By Phonology Technology

SLMs Outperform Competitors Yet Suffer Rapid Adversarial Jailbreaks
Thu Feb 06 2025 By Phonology Technology

Adversarial Settings and Random Noise Reveal Speech LLM Vulnerabilities
Thu Feb 06 2025 By Phonology Technology

Adversarial Attacks Challenge the Integrity of Speech Language Models
Thu Feb 06 2025 By Phonology Technology
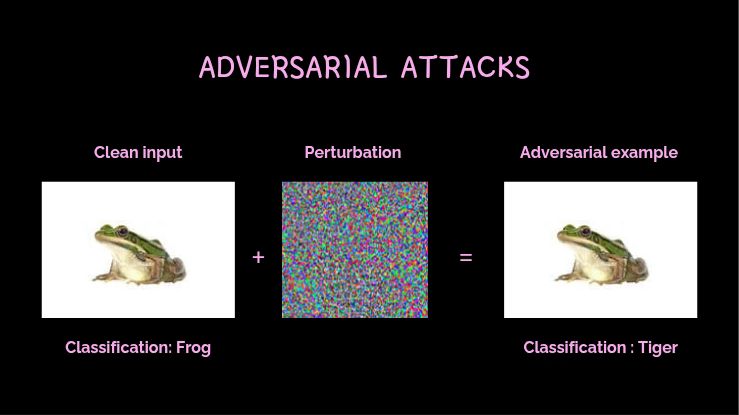
Adversarial Machine Learning Is Preventing Bad Actors From Compromising AI Models
Mon Jan 06 2025 By Praise James

Examining the Adversarial Test Accuracy of Later Exits in NEO-KD Networks
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models

The Impact of Hyperparameters on Adversarial Training Performance
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models

Clean Test Accuracy and Adversarial Training via Average Attack
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models

How NEO-KD Reduces Adversarial Transferability and Improves Accuracy
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models

How Ensemble Strategies Impact Adversarial Robustness in Multi-Exit Networks
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models
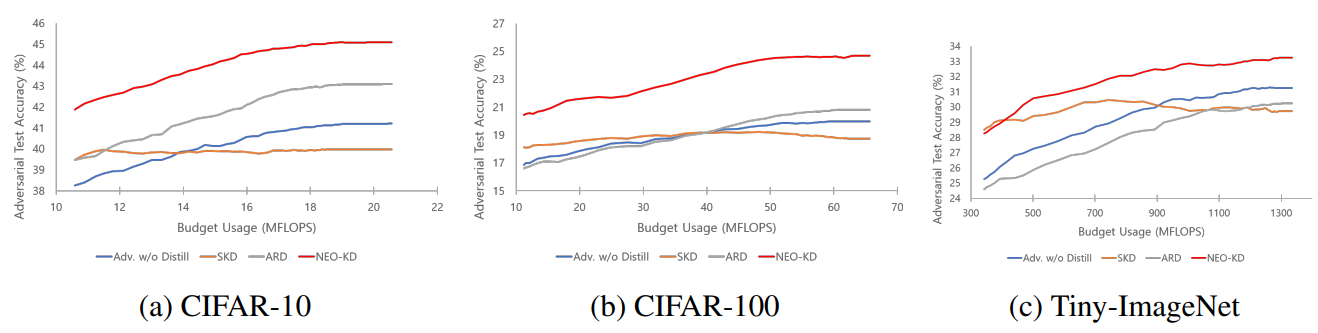
How NEO-KD Saves Up to 81% of Computing Power While Maximizing Adversarial Accuracy
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models

Benchmarking NEO-KD on Adversarial Robustness
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models
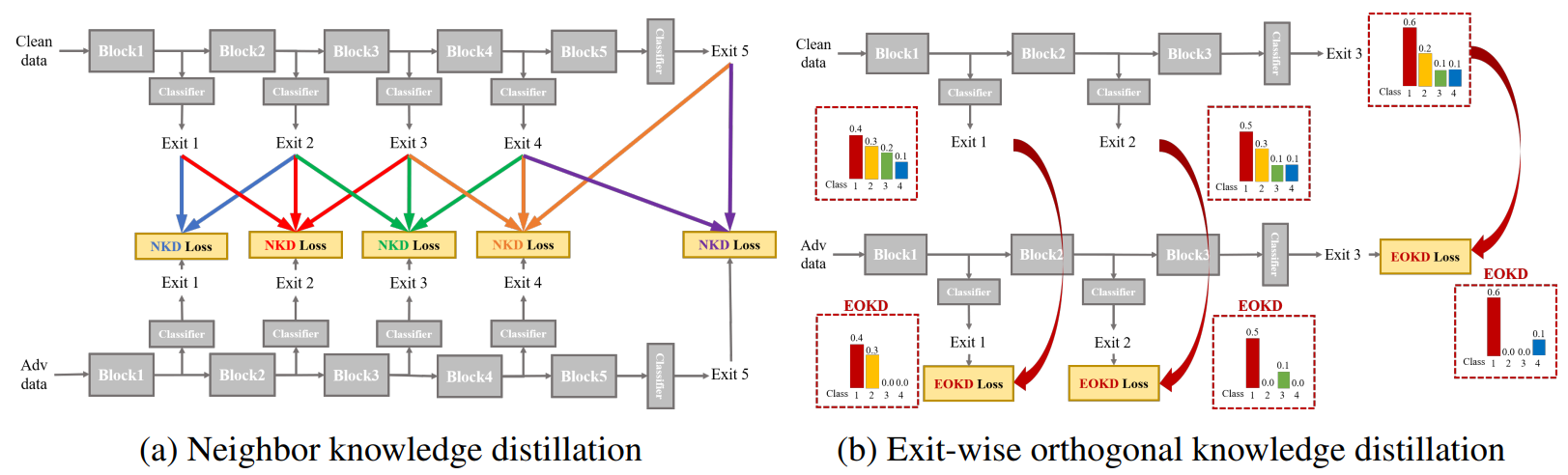
Adversarial Training in Multi-Exit Networks: Proposed NEO-KD Algorithm and Problem Setup
Mon Sep 30 2024 By Writings, Papers and Blogs on Text Models

Knowledge-Distillation-Based Adversarial Training for Robust Multi-Exit Neural Networks
Mon Sep 30 2024 By EScholar: Electronic Academic Papers for Scholars
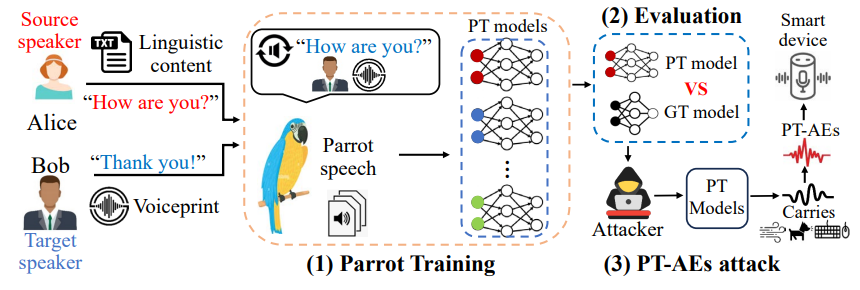
Understanding Speaker Recognition and Adversarial Speech Attacks
Tue Jun 11 2024 By BotBeat.Tech: Trusted Generative AI Research Firm
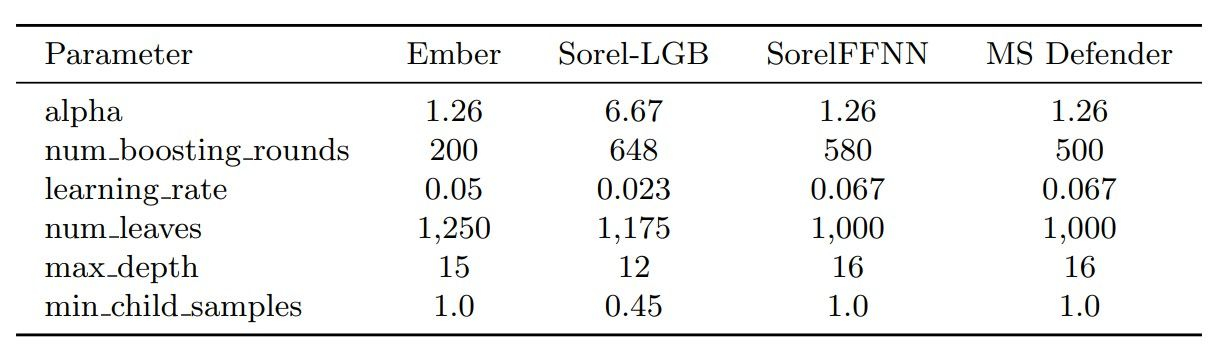
Adversarial Malware Creation with Model-Based Reinforcement Learning: Appendix
Thu Apr 18 2024 By Memeology: Leading Authority on the Study of Memes

Enhancing Cybersecurity with MEME: Reinforcement Learning for Adversarial Malware Evasion
Thu Apr 18 2024 By Memeology: Leading Authority on the Study of Memes


