2,132 reads
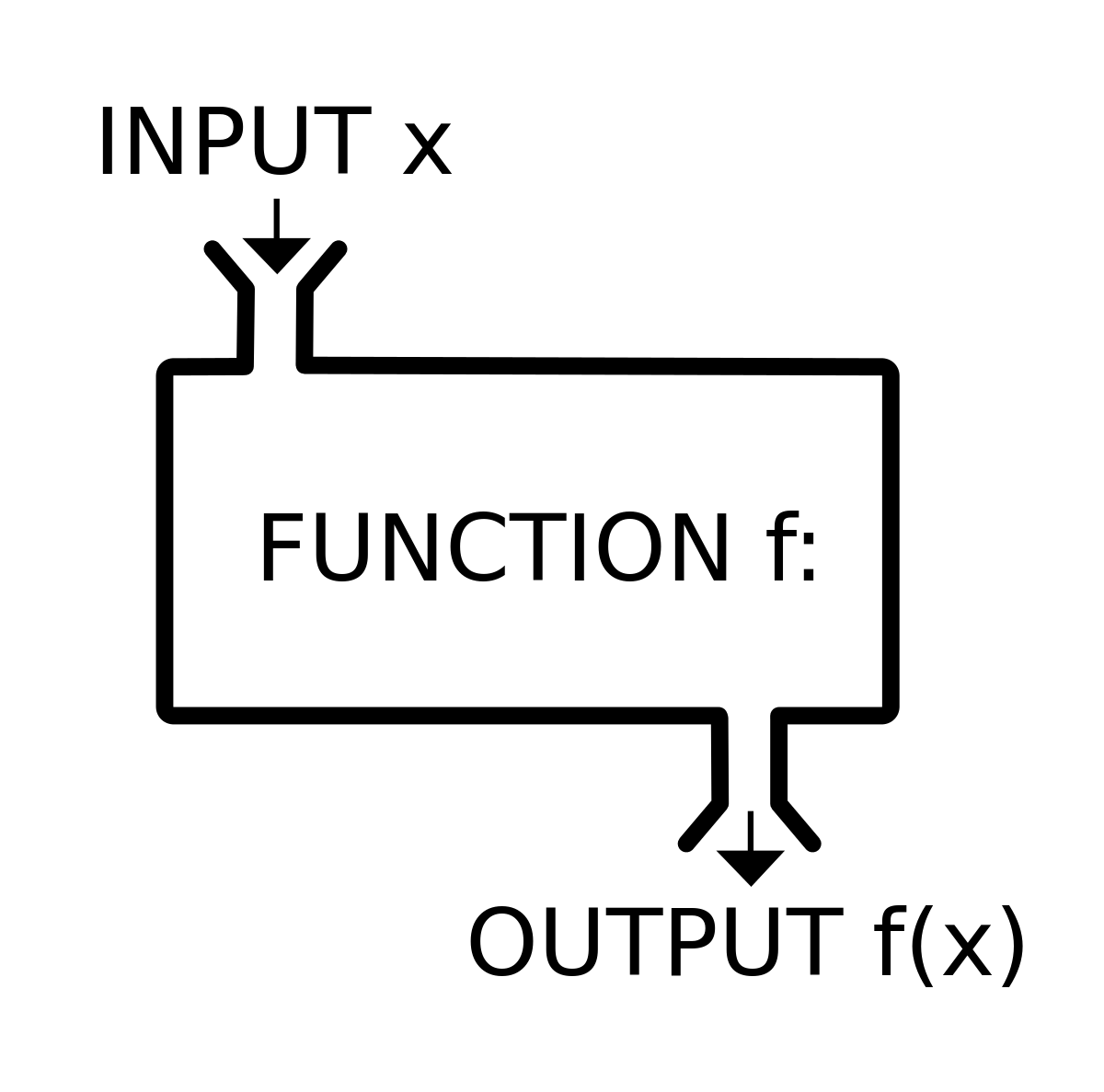
A Simple Introduction to One-Way Functions
by
October 10th, 2018
Audio Presented by
A tech enthusiast who loves making sense of complex technologies and sharing those learnings with fellow curious minds.
About Author
A tech enthusiast who loves making sense of complex technologies and sharing those learnings with fellow curious minds.