639 reads
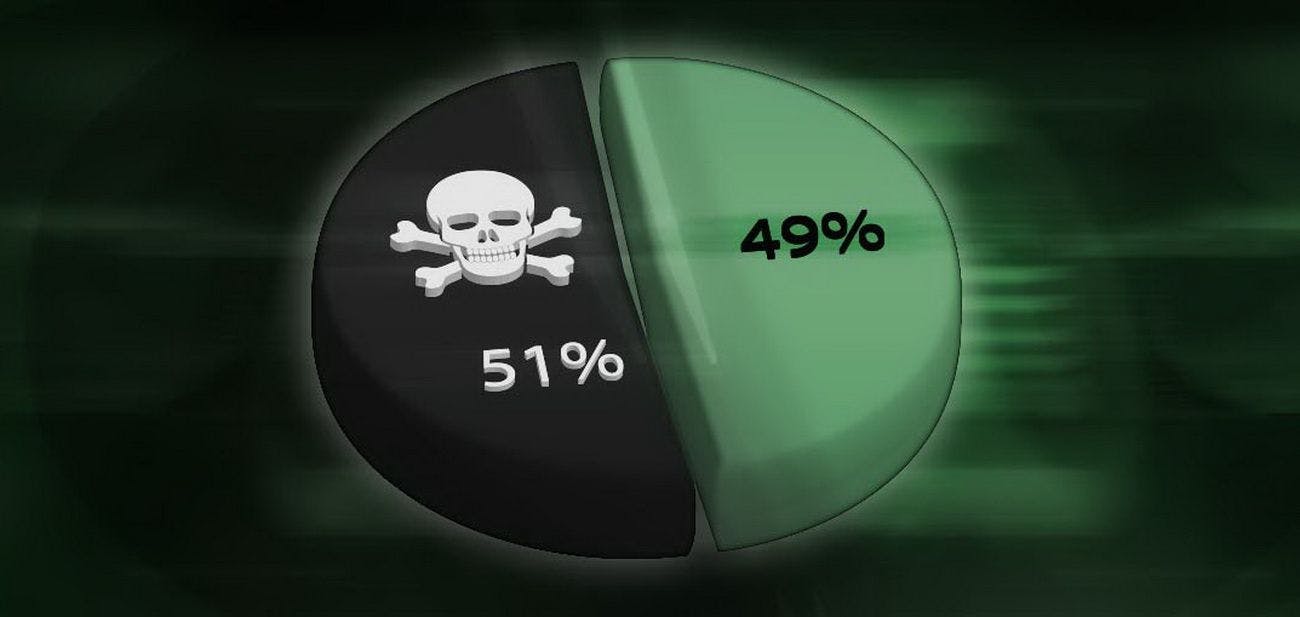
51% Attacks Pose the Biggest Threat to Smaller Mining-Based Cryptocurrencies
by
February 4th, 2021
Fintech journalist. My works are featured by Cointelegraph, Investing, SeekingAlpha.
About Author
Fintech journalist. My works are featured by Cointelegraph, Investing, SeekingAlpha.