12,710 reads
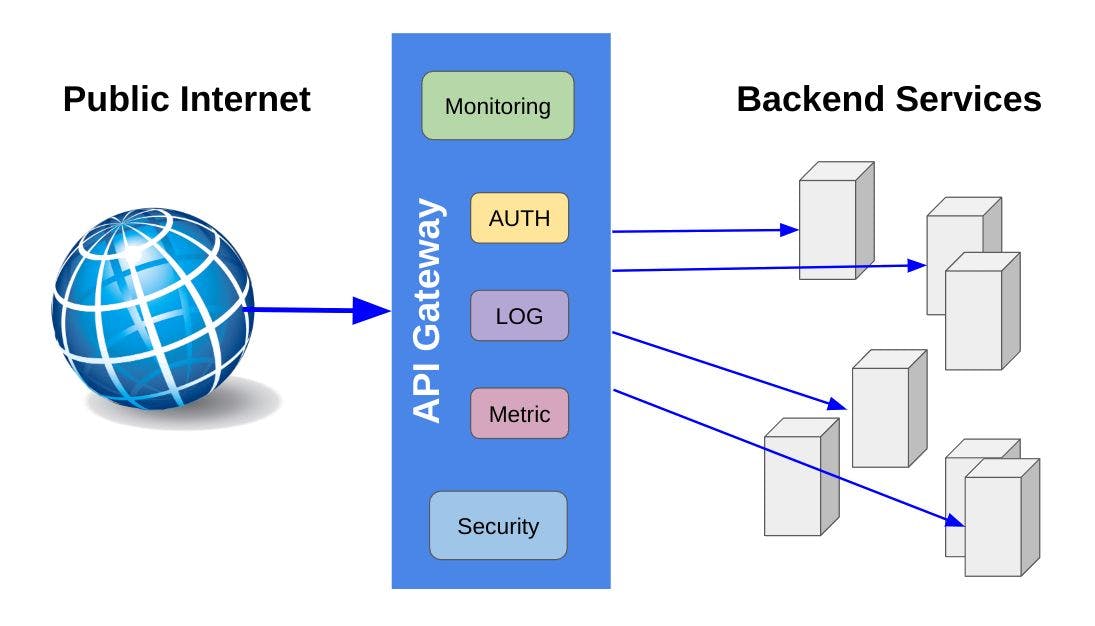
The Anatomy of an API Gateway in Golang
by
June 12th, 2023
Audio Presented by

I am an independent software engineer working in information technology since the early 90s.
Story's Credibility

About Author
I am an independent software engineer working in information technology since the early 90s.
Comments
TOPICS
Related Stories
10 Threats to an Open API Ecosystem
Jul 18, 2022