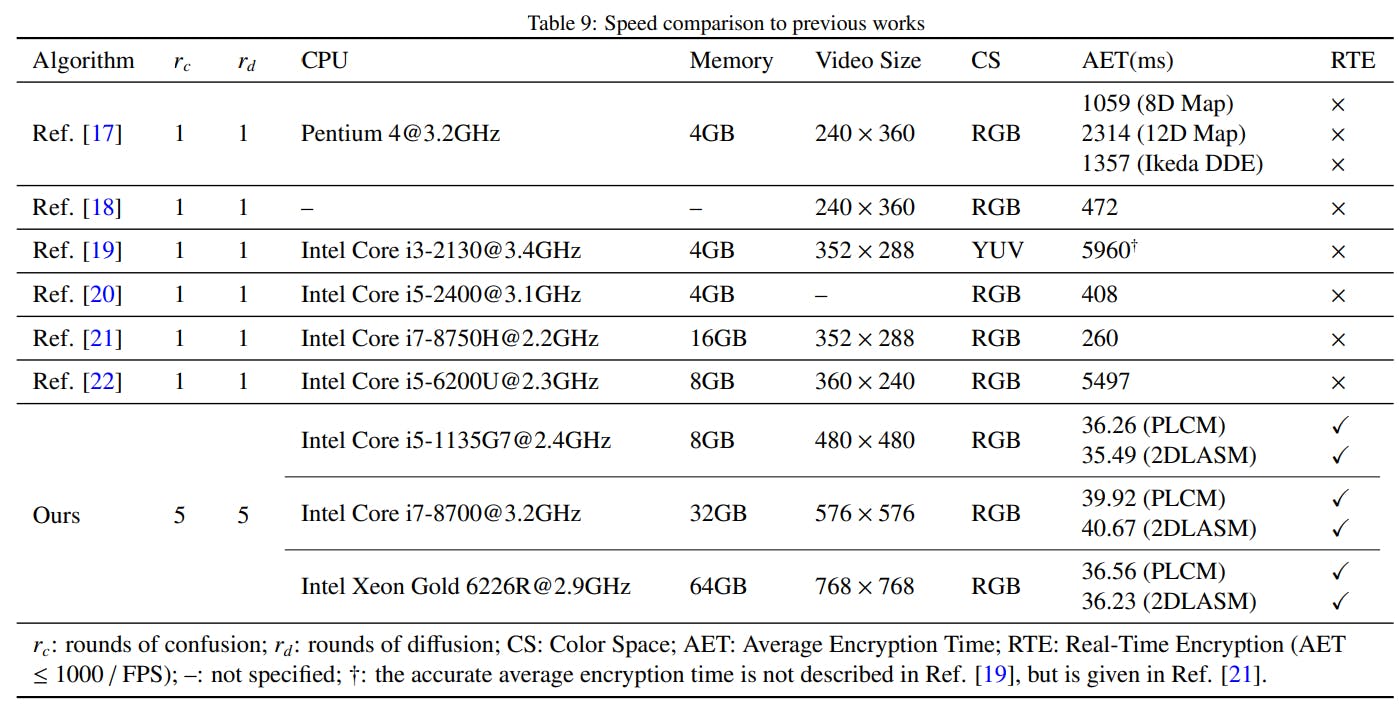
149 reads
Strides in Real-Time Video Encryption: Comparison To Previous Works
by
March 16th, 2024
Audio Presented by

Research to enable more than one user at a time without requiring multiple copies of the program running on the computer
About Author
Research to enable more than one user at a time without requiring multiple copies of the program running on the computer