4,856 reads
Practical Smart Contract Security Analysis and Exploitation— Part 1

Too Long; Didn't Read
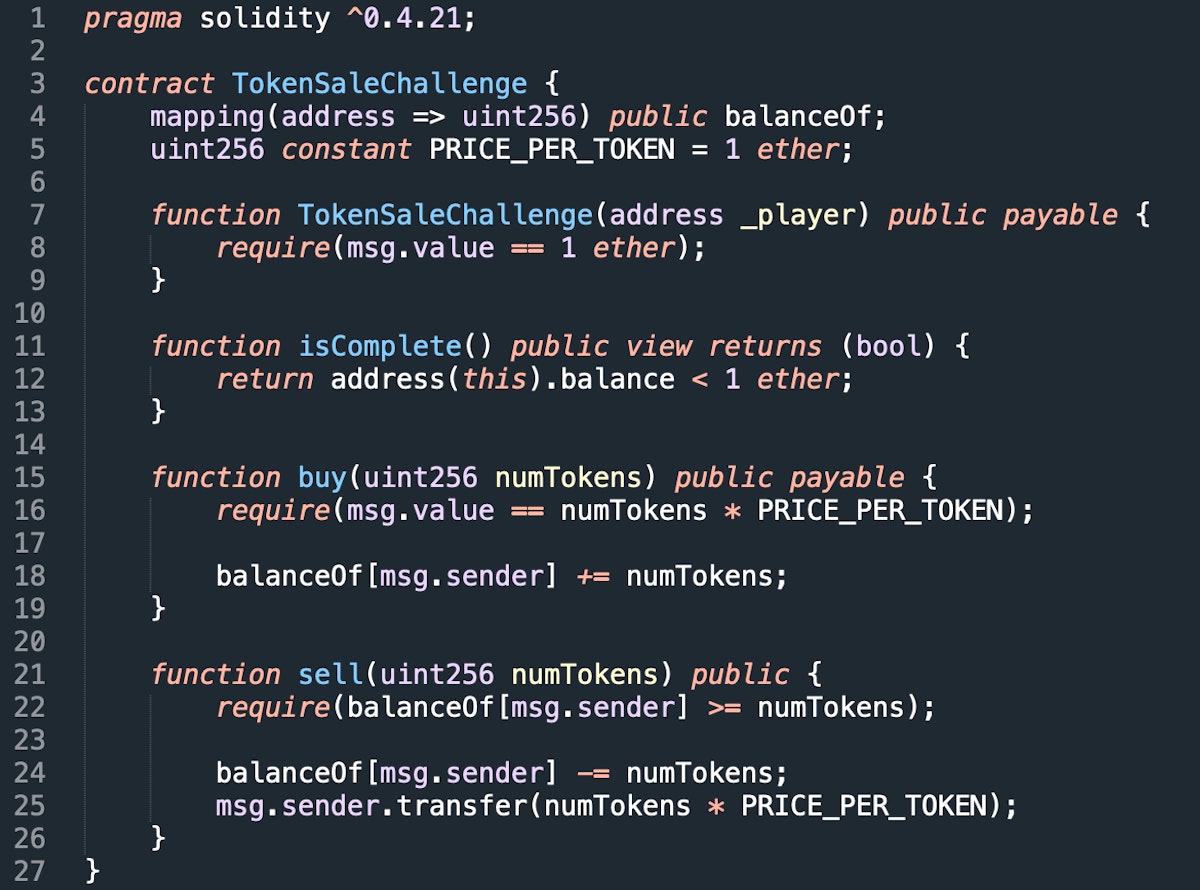
<em>In this article I explain how to use </em><a href="https://github.com/ConsenSys/mythril-classic" target="_blank"><em>Mythril</em></a><em> to find and exploit security bugs in Ethereum smart contracts. The articles will cover basic principles and advanced techniques, such as testing security properties, proving invariants, analyzing multi-contract systems and auto-looting ETH from vulnerable contracts on the Ethereum network.</em>L O A D I N G
. . . comments & more!
. . . comments & more!