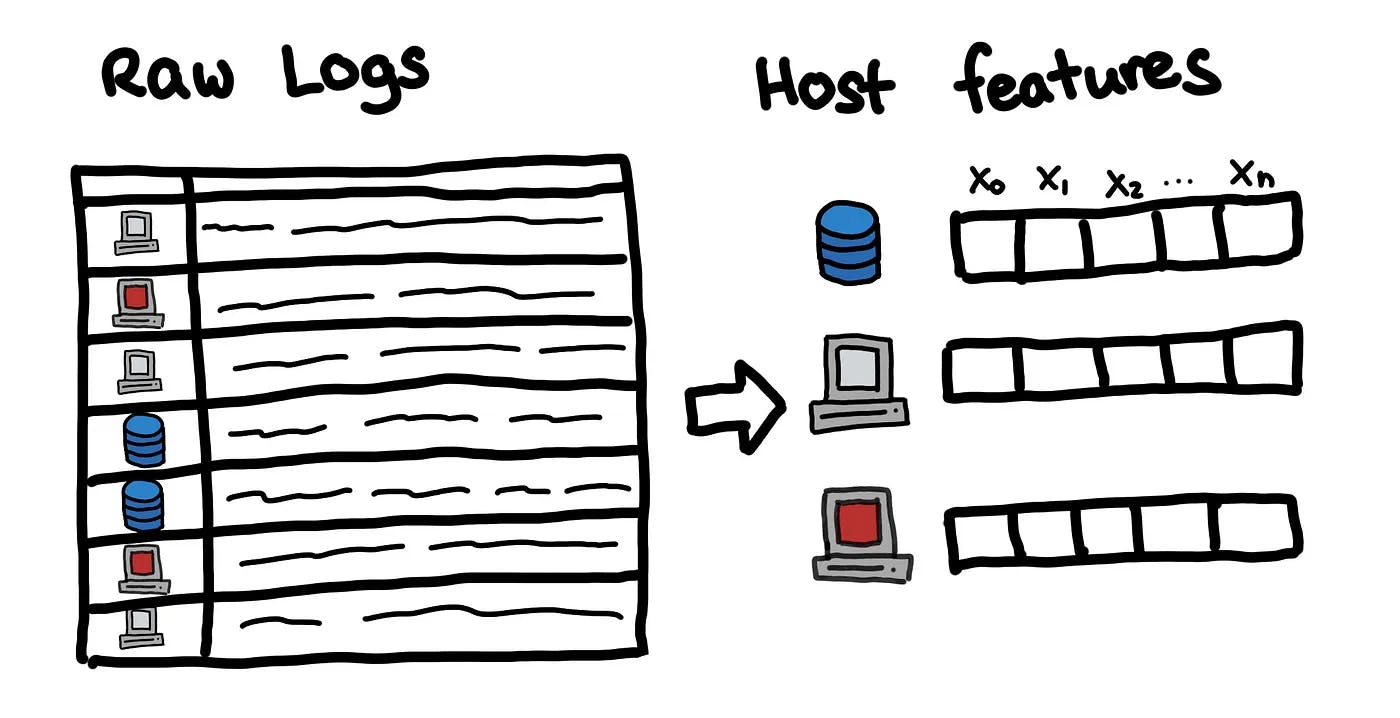
254 reads
Practical Feedback on Using Machine Learning in Information Security
by
April 29th, 2024
Audio Presented by

Senior Software Engineer at WhatsApp! Where I build products and protect our billions of users, preventing abuse and ensuring your online safety.
Story's Credibility

About Author
Senior Software Engineer at WhatsApp! Where I build products and protect our billions of users, preventing abuse and ensuring your online safety.