912 reads
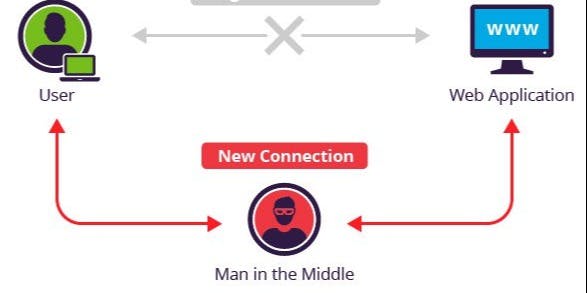
What is a Man In The Middle Attack? Eavesdropping at its best.
by
September 12th, 2019
A versatile and motivated professional with an ardent interest in Cyber Security and Music Product
About Author
A versatile and motivated professional with an ardent interest in Cyber Security and Music Product
Comments
TOPICS
Related Stories
HTTP and Web Servers
Aug 28, 2019
HTTP and Web Servers
Aug 28, 2019