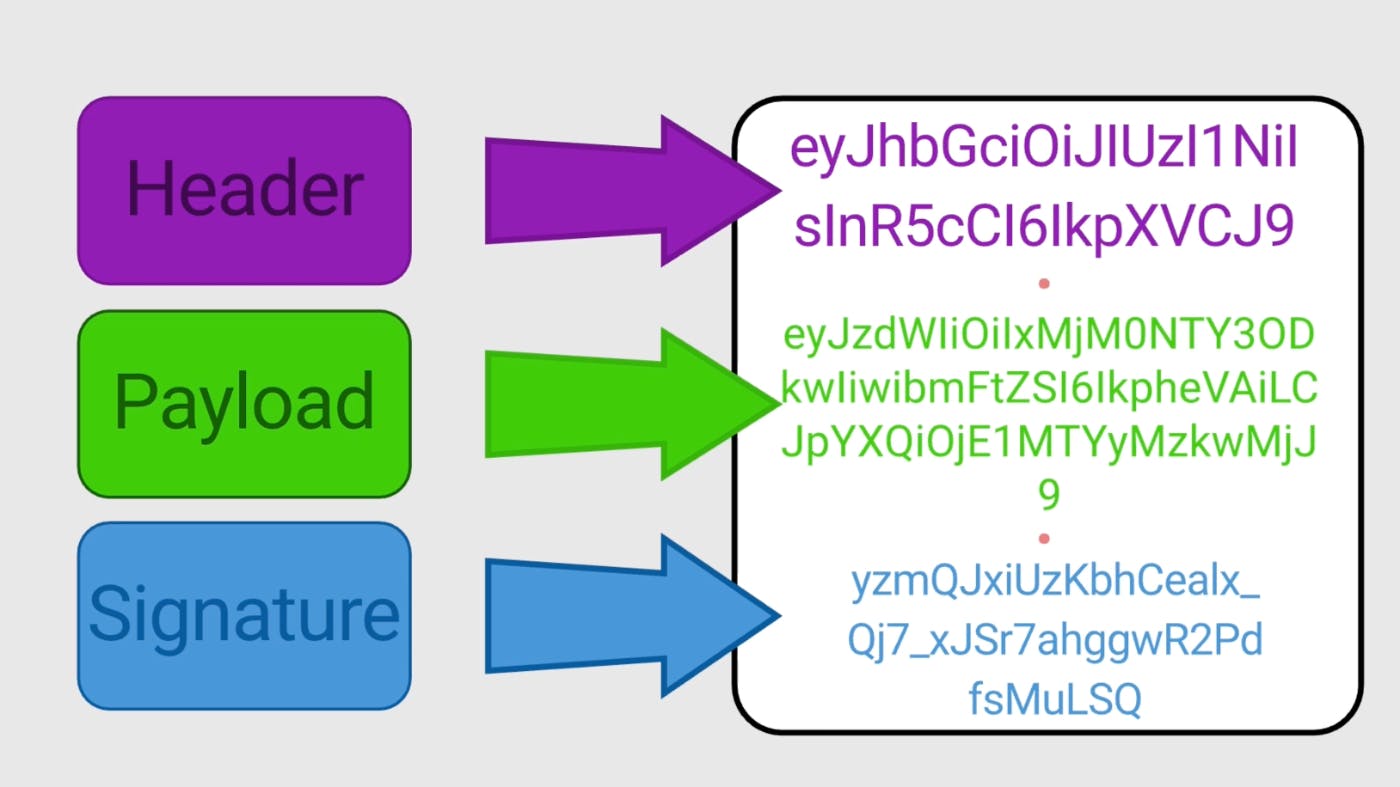
412 reads
JWT Explained in 4 Minutes, With Visuals
by
February 28th, 2024
Audio Presented by

Continuously read and learn about web and mobile development 🧑🏻💻. Also loves meat 🍗.
Story's Credibility



About Author
Continuously read and learn about web and mobile development 🧑🏻💻. Also loves meat 🍗.