2,135 reads
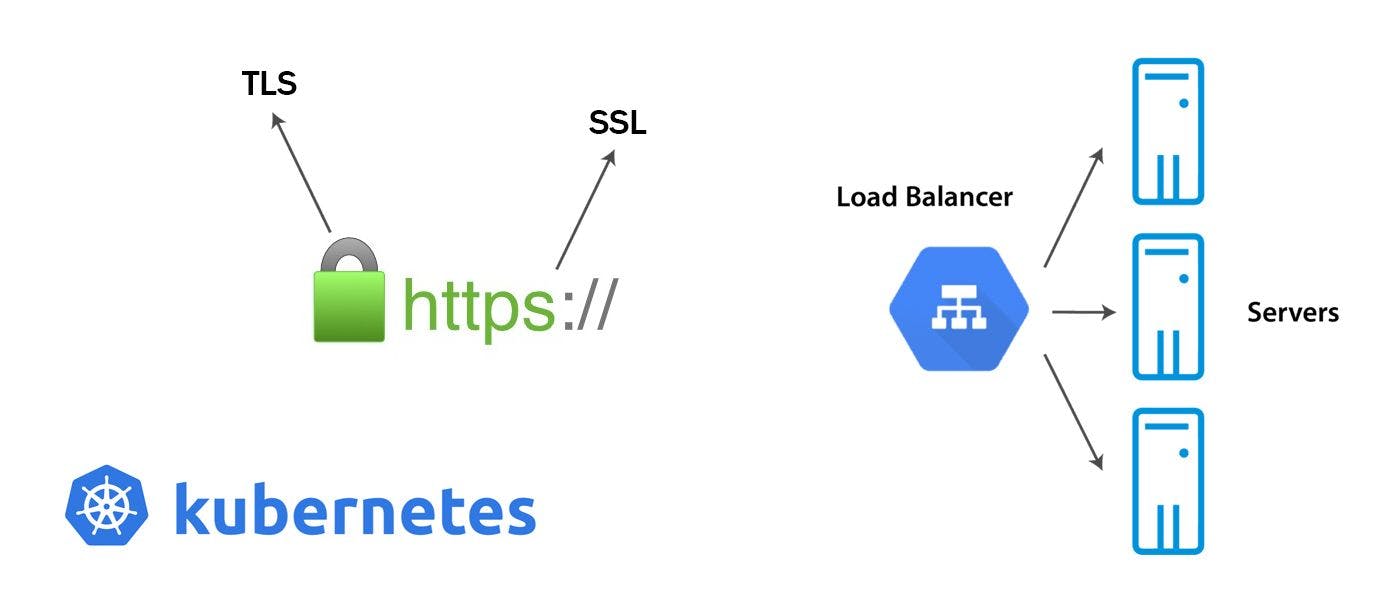
How to implement TLS OR SSL and set up HTTP(S) Load Balancing with Ingress for the Kubernetes API
by
September 24th, 2021

Software and Web Application Developer at Nexsoftsys - Software Development Company
About Author
Software and Web Application Developer at Nexsoftsys - Software Development Company
Comments
TOPICS
Related Stories
10 Threats to an Open API Ecosystem
Jul 18, 2022