1,172 reads
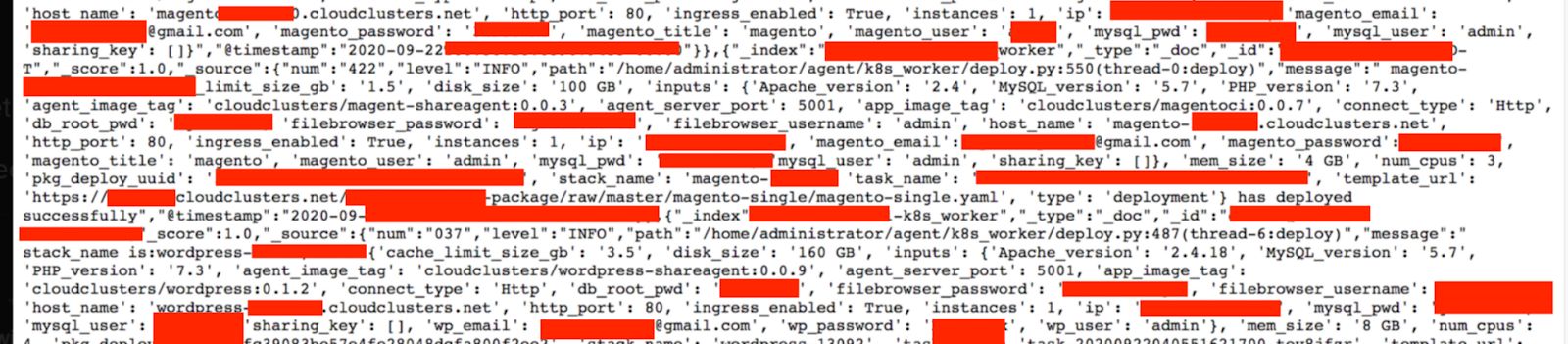
Hosting Provider Cloud Clusters Inc. Potentially Exposed 63M Records
by
November 18th, 2020
Audio Presented by
Avid techie. Attached via cord to NES/SNES/N64. Freelance writer. AZ born, world traveler.
About Author
Avid techie. Attached via cord to NES/SNES/N64. Freelance writer. AZ born, world traveler.