493 reads
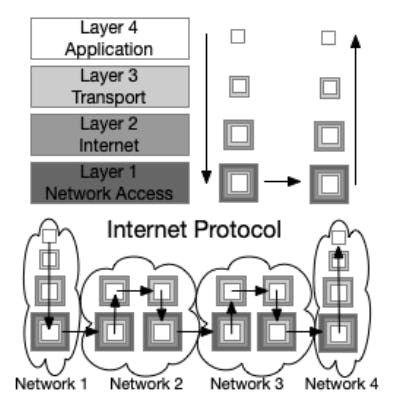
Layers of Encapsulation: Exploring the TCP/IP Model in Internet Communication
by
April 4th, 2024
Audio Presented by

At NetNeutrality.Tech we treat all data on the Internet the same way and all users have equal access to online content.
Story's Credibility

About Author
At NetNeutrality.Tech we treat all data on the Internet the same way and all users have equal access to online content.